LEISec
Laboratory for Experimental Information Security
LEISec is a research lab, headed by Eran Tromer, in Tel Aviv University's School of Computer Science. The lab's goal is to investigate the challenges of cryptography and information security in the real world, to identify and analyze new threats, and to develop new methods for protecting information, computers and networks. The lab takes a hands-on approach, emphasizing empirical evaluation and concrete system implementations.
A main current focus is on physical information leakage from complex systems, such as laptop PCs. Our most recent publications on this topic are:

Daniel Genkin, Noam Nissan, Roei Schuster, Eran Tromer,
Lend Me Your Ear: Passive Remote Physical Side Channels on PCs
proc. USENIX Security 2022, to appear
Daniel Genkin, Mihir Pattani, Roei Schuster, Eran Tromer,
Synesthesia: Detecting Screen Content via Remote Acoustic Side Channels
proc. IEEE Symposium on Security & Privacy (S&P) 2019, to appear
Roei Schuster, Vitaly Shmatikov, Eran Tromer,
Situational Access Control in the Internet of Things,
proc. ACM Conference on Computer and Communications Security (CCS) 2018, 1056-1073, ACM, 2018
Daniel Genkin, Lev Pachmanov, Eran Tromer, Yuval Yarom,
Drive-by Key-Extraction Cache Attacks from Portable Code
proc. Applied Cryptography and Network Security (ACNS) 2018), LNCS 10892, 83-102, Springer, 2018
Roei Schuster, Vitaly Shmatikov, Eran Tromer,
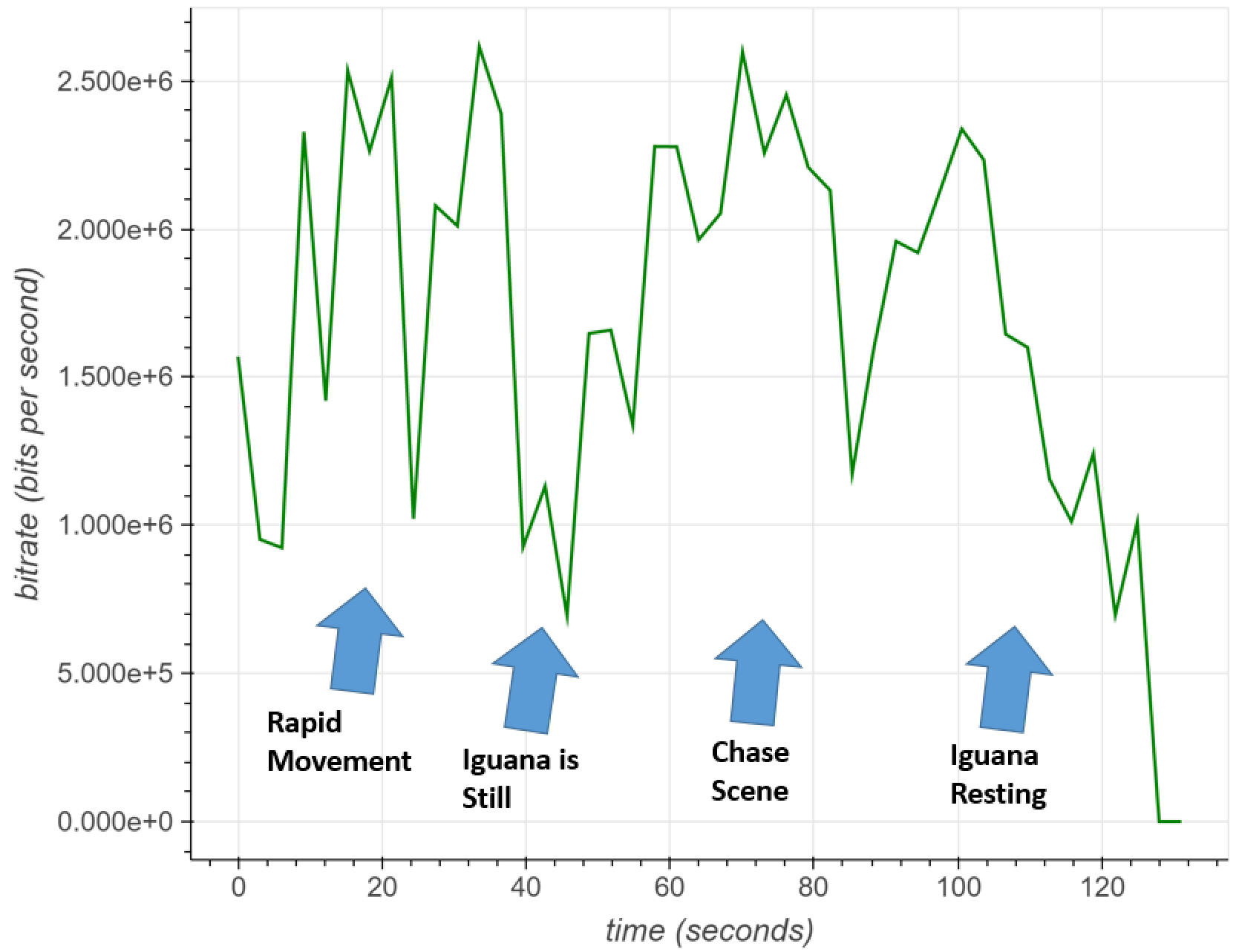
Beauty and the Burst: remote identification of encrypted video streams
proc. USENIX Security 2017, to appear
Daniel Genkin, Lev Pachmanov, Itamar Pipman, Adi Shamir, Eran Tromer, Yuval Yarom,
Physical key extraction attacks on PCs
Communications of the ACM, vol. 59 no. 6, 70-79, 2016
Daniel Genkin, Lev Pachmanov, Itamar Pipman, Eran Tromer, Yuval Yarom,
ECDSA key extraction from mobile devices via nonintrusive physical side channels,
ACM Conference on Computer and Communications Security (CCS) 2016, 1626-1638, 2016
Yuval Yarom, Daniel Genkin, Nadia Heninger,
CacheBleed: a timing attack on OpenSSL constant time RSA
proc. Workshop on Cryptographic Hardware and Embedded Systems (CHES) 2016, LNCS 9813, 346-367, 2016
Roei Schuster, Eran Tromer,
DroidDisintegrator: intra-application information flow control in Android apps,
proc. ACM Symposium on Information, Computer and Communications Security (ASIACCS) (ASIACCS) 2016, to appear
Daniel Genkin, Lev Pachmanov, Itamar Pipman, Eran Tromer,
ECDH key-extraction via low-bandwidth electromagnetic attacks on PCs,
proc. RSA Conference Cryptographers' Track (CT-RSA) 2016, LNCS 9610, 219-235, Springer, 2016
Almog Benin, Sivan Toledo, Eran Tromer,
Secure Association for the Internet of Things,
International Workshop on Secure Internet of Things (SIOT) 2015.
Daniel Genkin, Lev Pachmanov, Itamar Pipman, Eran Tromer,
Stealing keys from PCs using a radio: cheap electromagnetic attacks on windowed exponentiation,
proc. Workshop on Cryptographic Hardware and Embedded Systems (CHES) 2015, LNCS 9293, 207--228, Springer, 2015
Daniel Genkin, Itamar Pipman, Eran Tromer,
Get your hands off my laptop: physical side-channel key-extraction attacks on PCs,
proc. Workshop on Cryptographic Hardware and Embedded Systems (CHES) 2014, LNCS 8731, 242-260, Springer, 2014
Daniel Genkin, Itamar Pipman, Eran Tromer,
Get your hands off my laptop: physical side-channel key-extraction attacks on PCs (extended version),
Journal of Cryptographic Engineering, vol. 5 no. 2, 95--112, 2015
Daniel Genkin, Adi Shamir, Eran Tromer,
RSA key extraction via low-bandwidth acoustic cryptanalysis,
proc. CRYPTO 2014, part I, LNCS 8616, 444-461, 2014
Daniel Genkin, Adi Shamir, Eran Tromer,
Acoustic cryptanalysis,
Journal of Cryptology, to appear
- [web page with summary and Q&A]
- [pdf: extended version] [eprint]
- [CRYPTO'14 presentation on YouTube] (slides+voice, but does not show the on-stage demo)
Other publications by lab members on information leakage from PCs include:
Thomas Ristenpart, Eran Tromer, Hovav Shacham, Stefan Savage,
Hey, you, get off of my cloud! Exploring information leakage in third-party compute clouds,
proc. ACM Conference on Computer and Communications Security (CCS) 2009, 199-212, ACM, 2009
Eran Tromer, Dag Arne Osvik, Adi Shamir,
Efficient cache attacks on AES, and countermeasures,
Journal of Cryptology, vol. 23 no. 1, 37-71, Springer, 2010
Dag Arne Osvik, Adi Shamir, Eran Tromer,
Cache attacks and countermeasures: the case of AES,
proc. RSA Conference Cryptographers' Track (CT-RSA) 2006, LNCS 3860, 1-20, Springer, 2006
- [pdf: extended version] [ps.gz]
- See journal version above.
- First presented at the FSE 2005 rump session, February 2005 (see below)
A typical day at LEISec