Our Goal
The existing permissions and capabilities systems in mobile platforms allow expressing assurances in terms of resources used by apps. Users, however, should care, and do care, about security risks. These risks are often expressible in terms of the possible information flow from information sources to sinks. For example, a user of a voice recorder app with permission to access the internet ("to display ads") should be assured that recordings are never sent over the network. We built a system, DroidDisintegrator, which applies information flow control (IFC) on Android apps.
DroidDisintegrator can express and enforce information flow assurances for existing legacy code, as well as help developers build tightly constrained apps in an intuitive and automated process.
IFC Granularity
Despite intensive research efforts on applying IFC on many platforms, IFC has not been widely adopted in any mainstream programming practice.
The typical structure of Android apps offers an opportunity for a novel and effective application of IFC. In Android, an app consists of a collection of a few dozen "components", each in charge of some high-level functionality. Most components do not require access to most resources. These components are a natural and effective granularity at which to apply IFC (as opposed to the typical process-level or language-level granularity). By assigning different permission labels to different components, and limiting information flow between components, it is possible to express and enforce IFC constraints.
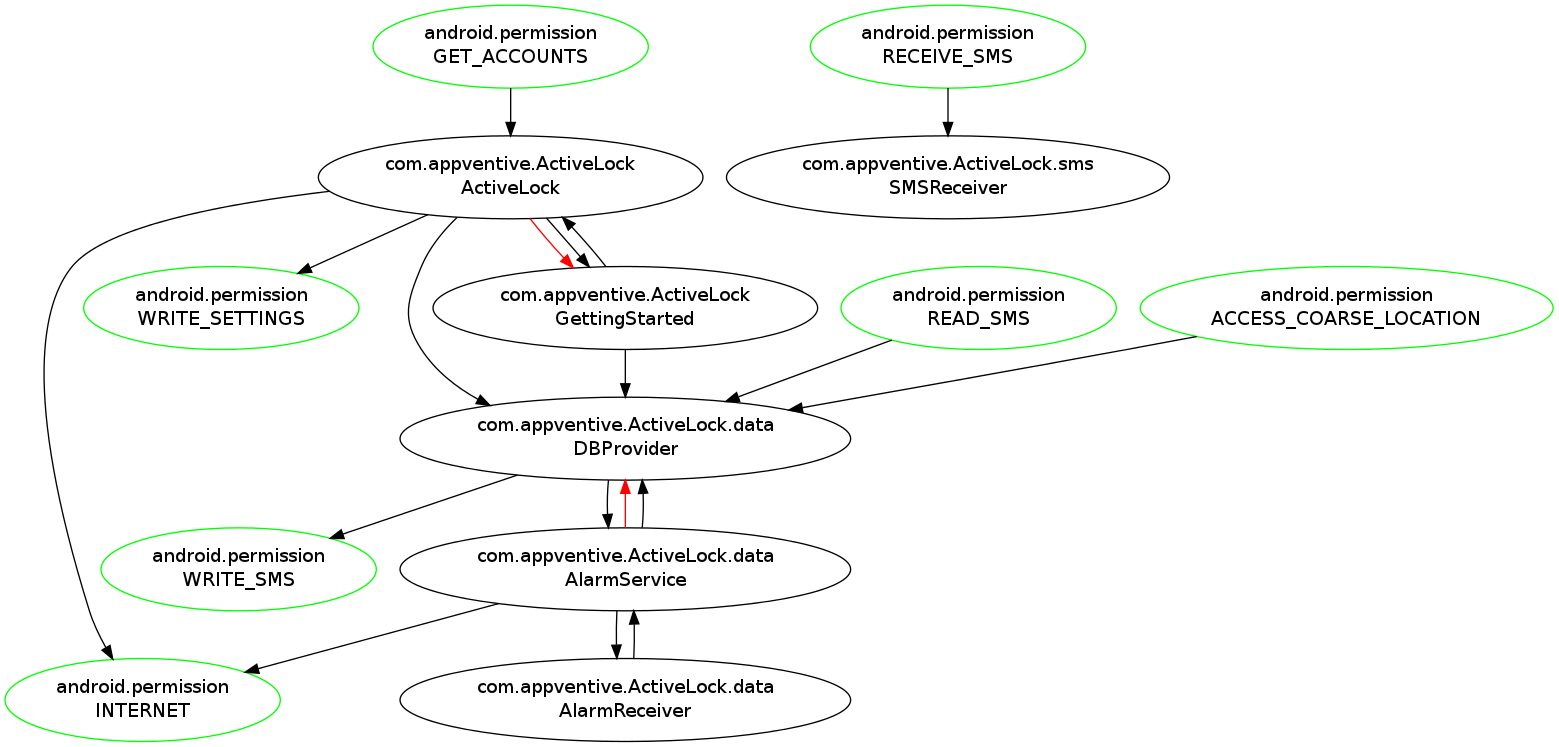
Employing component level IFC to Executive Assist (see above graph), we can enforce the constraint, e.g., "SMS does not reach the Internet" by granting the SMS_RECEIVE permission only to SMSReceiver component and limiting its communication with the rest of the app components. This provides important guarantees to the user without breaking app functionality.
DroidDisintegrator Workflow: "Fail-safe" App Analysis
DroidDisintegrator uses dynamic information flow analysis to generate IFC policies for Android apps, repackages apps to embed these policies, and enforces the policies at runtime. The analysis phase is automated by employing an event fuzzer.
Crucially, DroidDisintegrator uses information flow analysis differently from most previous work. I.e., analysis is for the purpose of policy generation rather than for discovery of malicious information leaks. Thus, analysis errors do not break security guarantees: analysis false negatives may, at worst, result in broken app functionality. Analysis false positives may only result in an overly permissive policy. Either way, the information flow assurances derivable from the policy, and presented to the user, are enforced.
Paper
- Roei Schuster, Eran Tromer, DroidDisintegrator: Intra-Application Information Flow Control in Android Apps, proc. ACM Symposium on Information, Computer and Communications Security (ASIACCS) 2016, 401-412, ACM, 2016
- Latest version: [PDF]
This research was conducted at the Laboratory for Experimental Information Security (LEISec).
This work was supported by the Check Point Institute for Information Security; by a Google Faculty Research Award; by the Israeli Ministry of Science and Technology; by the Israeli Centers of Research Excellence I-CORE program (center 4/11); and by the Leona M. & Harry B. Helmsley Charitable Trust.


